Spending money on your business is always a difficult decision, especially on areas that do not directly have a return on revenue. As a business owner, and maybe a new business owner, where do you spend those precious dollars? I recently asked my LinkedIn community, made up of mostly current and prior coworkers and those in the IT security community, the following question:
“You’re a small (5-50 person) company and only have $10,000 to spend on information security in 2023. Where/how do you spend that money? I’m leaving this really open ended. No regard to regulatory requirements or industry vertical. You only have $10,000.”
With more than 30,000 views and 100 responses, the overwhelming advice was to perform a risk assessment and enable multi-factor authentication (MFA), followed closely by employee security awareness training.
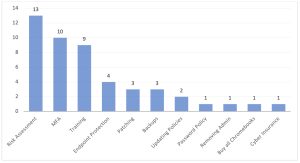
The idea behind performing the risk assessment is that you can’t manage what you don’t know you have. Furthermore, performing the assessment will help you direct future dollars. For example, the assessment may help you determine that you are storing critical customer information in areas you hadn’t realized. Maybe with this information you figure out you need to encrypt the data, back it up, or even remove it all together. Performing a risk assessment doesn’t need to take months and tens of thousands of dollars from consultants. While they can bring outside expert advice, there are free assessment tools from independent organizations to assist.
You may need to use an assessment specific to your industry, but if you’re wondering where to start, consider these four steps:
Step 1: Prepare for the assessment, and define the scope
Step 2: Identify your assets, threats, and vulnerabilities
Step 3: Communicate the results
Step 4: Prioritize the risks, remediate, and document the results
If you are looking for a more comprehensive program for conducting risk assessments, consider the National Institute of Standards and Technology (NIST) 800-30 publication. It is designed for assessing federal information systems but provides a thorough framework that any organization can leverage. While the nearly 100-page guide may be overkill for your company, its high-level topics can easily be followed.
Second highest from the respondents was the need to enable multi-factor authentication. While not the number 1 answer in the results, enabling MFA shouldn’t be something to perform after the results of the assessment. You can enable MFA, today. Your email provider, banking, and VPN solution (if you use it) each have the option for MFA, and it should be turned on immediately. The easiest way for a malicious actor to get in is to brute force login passwords; MFA helps to protect against these attacks. While some MFA methods are better than others (phone-based SMS is not considered as secure anymore because of SIM swapping), there are free MFA tools from Microsoft and Google giving you the ability to set this up easily. Consider what would happen if someone gained access to your email. Not only would they have sensitive and confidential information, but they can also impersonate you, and use your email account to confirm the reset of passwords for other business systems.
Third was employee security awareness training. There is no magic bullet or special software that is more effective at protecting your organization than helping your employees be vigilant when opening email links or surfing the web. It often only takes one click of a malicious link for the attacker to get a backdoor installed on the computer. And with that backdoor, they can move around your network, often undetected, searching for sensitive information, other passwords, or worse, encrypting and then holding ransom your data.
One “thinking outside the box” suggestion was to remove all computers and switch to Chromebooks. If all of your software and tools are cloud-based, it may be a good option to remove as much of your digital footprint as possible to make it that much harder for someone to break in. We’ve never come across a company that could be 100% cloud-based, but it’s something to consider.
Only one commenter suggested cyber insurance. Insurance is always a last stop. You wouldn’t not wear your seatbelt just because you have car insurance. You also shouldn’t take a defeatist attitude that there’s no way to stop the bad guys, so why try? As the business owner, your customers and employees are trusting you to safeguard their personal information, not only the company-sensitive information. Implement other preventative controls before leaving it to your cyber insurance policy. Additionally, many insurance providers are requiring you to prove you have a secure environment before they will provide coverage, and in some cases, requiring higher premiums if you fail to have adequate security.
Making $10,000 stretch anywhere in business can be difficult, but when asked of experts in the IT security industry, the overwhelming response was to implement protections that are free. These free steps will make your business less likely to be the next victim of ransomware. Enable MFA, ensure all software is set to auto-update for patches, and use separate passwords across each system. When we perform risk assessments, IT audits, or penetration tests, we find the root cause for many of the failures to be related to one of these three previous areas. Do this before spending any of that $10,000.




